Guideline on searching encrypted e-mails in response to information requests
1. Issue
When searching for records in response to an information request, a simple keyword search in an e-mail inbox will not do any of the following:
- scan information contained in the body of encrypted e-mails
- search the attachments of encrypted e-mails
In a simple keyword search, encrypted e-mails will only show up in the search results if the keywords used in the search are found in the subject line. Therefore, employees must search both the subject line of the encrypted e-mails and the content of the e-mails. Note that the search function in most e-mail software does not search text in scanned documents or images.
2. Context
There are various instances where government institutions are obligated to search for and produce information. Two notable examples are:
- the litigation discovery process
- requests under the Access to Information Act and the Privacy Act
In these and other cases, institutions must identify, preserve and collect all information resources that are relevant to the request.
Treasury Board policyFootnote 1 and information management (IM) practice dictate that:
- e-mails of business value should be transferred to a designated corporate repository as soon as possible
- transitory e-mails should be regularly deletedFootnote 2
All encrypted e-mails of business value should be decrypted and stored in the designated corporate repository in a manner appropriate to the security classification and sensitivity of the information within the e-mail. This guideline was developed to address situations where encrypted e-mails that respond to information requests remain in an e-mail inbox.
The obligation to disclose and produce records extends to all information resources regardless of:
- their format (for example, electronic or paper)
- whether they are considered information resources of business value or transitory records
- where they are stored
For information resources that exist as encrypted e-mails in employee inboxes, the content of these encrypted e-mails must be searchable in order to ensure that any records relevant to an information request are identified, preserved and collected.
Having standardized and rigorous IM practices will ensure that when requests for information arise, institutions are able to identify, preserve and collect relevant information resources in a way that:
- is thorough and cost-effective
- minimizes disruptions to departmental operations
3. Guidance
To ensure that all information relevant to a discovery process or a request for information can be identified, it is recommended that government institutions:
- Develop and implement processes and guidance to help users transfer e-mails of business value, including specific processes for transferring encrypted e-mails of business value, to the designated corporate repository in a timely manner.
- Develop and implement processes and guidance for searching the content of encrypted e-mails. A sample process for searching the content of encrypted e-mails in Outlook is provided in the Appendix. This process:
- is presented as an example of the kind of process that departments should have in place for searching e-mails
- does not represent the process that they must use
- Provide training and support to users on the proper processes for:
- searching the content of encrypted e-mails in response to information requests
- transferring e-mails of business value to the designated corporate repository in a timely manner
- Follow proper IM exit protocols for e-mail management when employees depart, including decrypting e-mails of business value and transferring them to the designated corporate repository in a manner appropriate to the security classification and sensitivity of the information within the e-mails.
4. Additional guidance
5. Further information
Contact DPPN@tbs-sct.gc.ca for any questions about this guideline.
6. Appendix: how to search for encrypted e-mails in Microsoft Outlook
Step 1: Before you start decrypting e-mails, verify who has proxy access to your e-mail folders in order to minimize the risk of unauthorized access to the custom search folder that you will create for your decrypted e-mails.
Step 2: To make encrypted sources of information searchable, set up a custom search folder.
Create a custom search folder in Microsoft Outlook
Creating a custom search folder can help you find e-mails. The search folder can be set to search any field in an Outlook e-mail. In this case, since we want to look for encrypted e-mails, you will need to create a custom search folder for encrypted e-mails.
- To create a custom search folder, open Microsoft Outlook, select the Folder tab on the ribbon, and then click on the New Search Folder button.
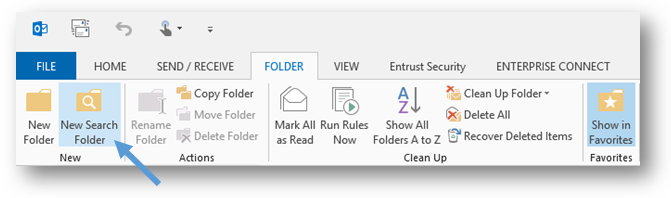
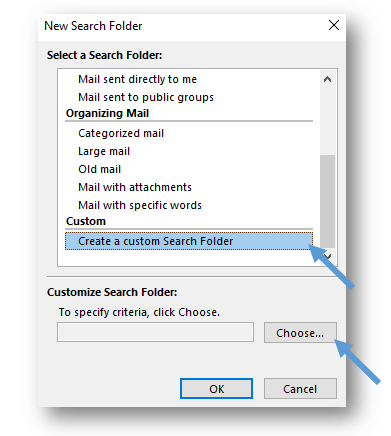
- In the New Search Folder window, scroll down to the bottom of the list. Select the Create a custom Search Folder option, and then click on the Choose button.
- In the Custom Search Folder window, type in a name for your folder. We suggest “Encrypted E-mails.”
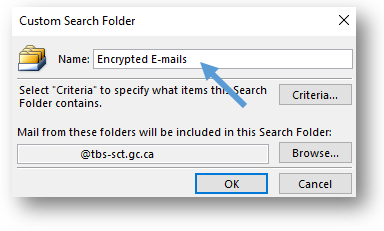
- Configure the criteria for the search. Click on the Criteria button and the Search Folder Criteria window will pop up.
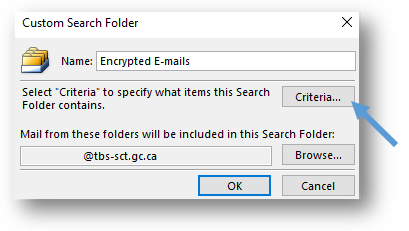
- In the Search Folder Criteria window, select the Advanced tab. This tab lets you add criteria based on all the fields that an Outlook e-mail can store.
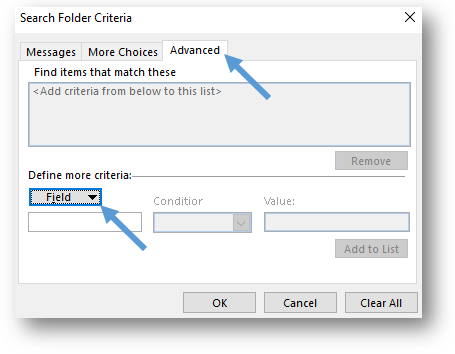
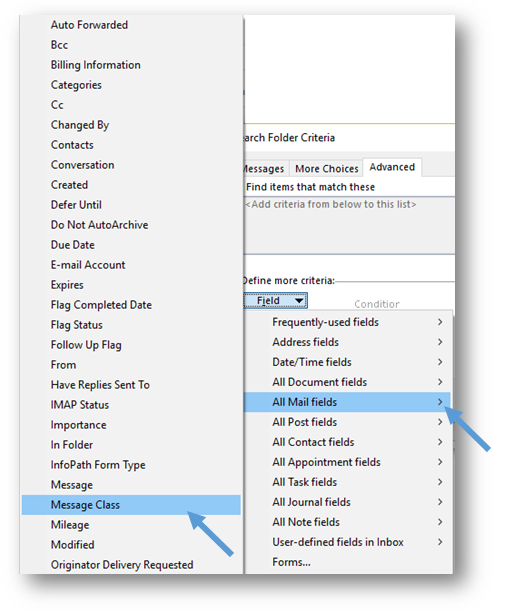
- Click on the Field button below Define more criteria and a drop-down menu will appear. From the drop-down menu, select All Mail fields and then Message Class.
- Under Condition, make sure that the drop-down menu says contains. Under Value, enter IPM.Note.SMIME in the empty field and click on the Add to List button.
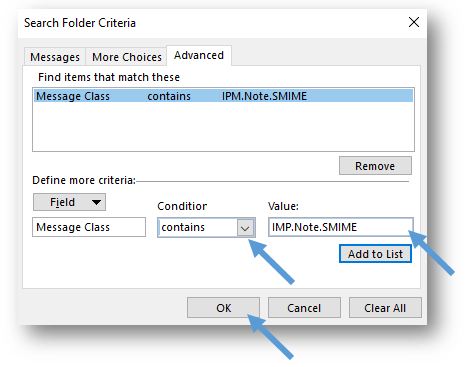
- When you are finished setting the criteria, click on the OK button to return to the Custom Search Folder window.
- By default, the custom search that you create will search your entire Outlook mailbox. If you want to conduct a search in specific mailbox, click on the Browse button.
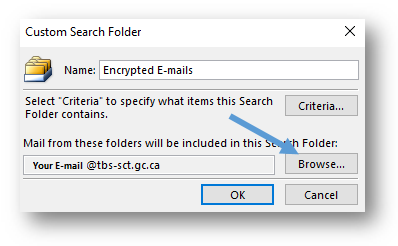
- In the Select Folder(s) window, select the mailbox that you want to include in the search. Click on the OK button once you are finished making your selection.
- You will return to the Custom Search Folder window. Click on OK.
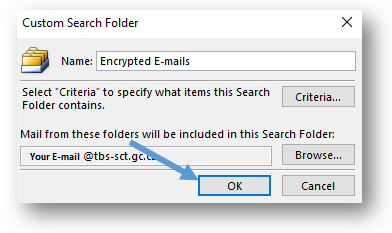
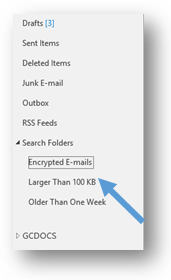
- In the New Search Folder window, click on the OK button. Outlook will then create the custom search folder and add it to your Outlook folder list on the left-hand side of the screen. You should be able to see your new Encrypted E-mails search folder under the Search Folders heading. The search that you have set up, by following the preceding steps, will be conducted automatically when you select the Encrypted E-mails search folder.
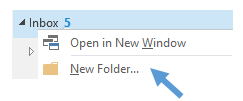
Create an Encrypted E-mails subfolder in your Inbox
- From your Inbox, create an Encrypted E-mails subfolder. You can do this by going to the Folder Pane, right-clicking on Inbox and selecting New Folder in the drop-down menu.
The Encrypted E-mail subfolder in your Inbox is where you will copy your encrypted e-mails so that you can decrypt them and search the content.
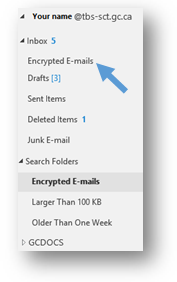
Step 3: Now that you have set up your Encrypted E-mails custom search folder and your Encrypted E-mails subfolder, you will need to log into Entrust before you can search through your encrypted e-mails.
- Log into Entrust by doing one of the following:
- clicking on the Entrust Security icon
- clicking on your Encrypted E-mail custom search folder or on an encrypted e-mail
The Entrust Security Store Login window will appear.
- In the login window, enter your password and click on OK. You will now be able to read your encrypted messages. *Note: Your Entrust session may timeout and you may be prompted to log back into Entrust.
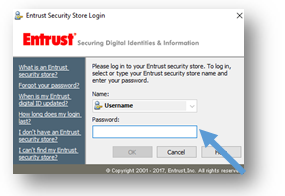
Step 4: Now that you are logged into Entrust, you will need to copy all of the encrypted e-mails in the Encrypted E-mails custom search folder into the Encrypted E-mails subfolder of your Inbox.
- Select all the e-mails in the Encrypted E-mails custom search folder by entering Ctrl + A. Then copy all the e-mails by entering Ctrl + C.
- Select the Encrypted E-mails subfolder in your Inbox and enter Ctrl + V to paste the copied e-mails into the subfolder.
- There are now copies of all the encrypted e-mails in your inbox in one folder (the Encrypted E-mail subfolder in your Inbox).
Step 5: Now that all of your encrypted e-mails have been copied to the Encrypted E-mails subfolder in your Inbox, you will need to decrypt them before you can search their contents.
- In your Inbox, go to your Encrypted E-mails subfolder and select up to 10 e-mails to decrypt at a time. To select e-mails, hold the Ctrl key while you click on the e-mails. Note that you cannot decrypt more than 10 e-mails at a time.
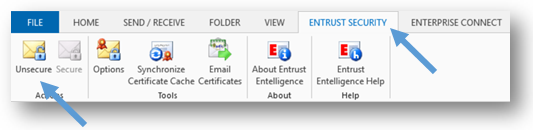
- To decrypt the e-mails that you have selected, select the Entrust Security tab in the Microsoft Outlook ribbon and click on the Unsecure icon. The selected e-mails are now decrypted. Keep repeating steps 1 and 2 until all the e-mails in your Encrypted E-mails subfolder are decrypted.
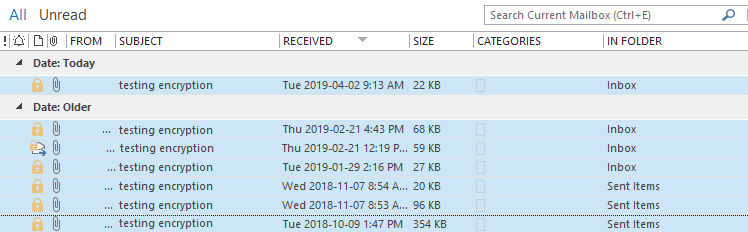
- In order to make searching and sorting e-mails in the Encrypted E-mails subfolder easier, make your Message List Pane in Outlook bigger until the search field and drop-down menu in your Outlook appear as they do in the figure below.
- From your Encrypted E-mails subfolder, click on the field above the e-mails that says search Encrypted E-mail (Ctrl + E), and enter your search term. Ensure that the Current Folder option is selected in the drop-down menu to the right of the field. Relevant results will then be displayed.
- Below the search field and the drop-down menu are column headings. Use the existing columns to help you sort your search results. Some useful headings that you should be able to see include:
- From
- Subject
- Received
- Importance (!)
- Once you have finished preparing your search, you must re-encrypt the emails in the Encrypted E-mails subfolder in your Inbox in order to protect this information from potential unauthorized access according to the Directive on Security Management.
- From the Encrypted E-mails subfolder, select all e-mails that you decrypted by entering Ctrl + A. Once you have selected all the e-mails that must be re-encrypted, select the Entrust Security tab again and click on the Secure button. Doing so will re-encrypt the e-mails.
- Once you have re-encrypted the emails in the Encrypted E-mails subfolder in your Inbox, you should delete this subfolder permanently by selecting the Encrypted E-mails folder then pressing the SHIFT + DELETE keys at the same time.